Examples¶
The scene¶
The Acme corporation has two business units: AutoMoto and ThingMoto.
Hannah, Acme's newly appointed ONEKEY admin, has received the following instructions from her Product Owner on how to set up access for the two teams:
- The two business units should have no visibility on each other's work (Acme's security guidelines are very strict).
- Acme has a product security team who is responsible for both business units. They should have access to all firmware and products.
- A third party vendor, Supplier Technology, develops firmware for some ThingMoto devices. They should be able to upload new firmware but have no visibility on the analysis results.
Setting up two business units¶
Hannah logs into ONEKEY and sets up the following permission structure:
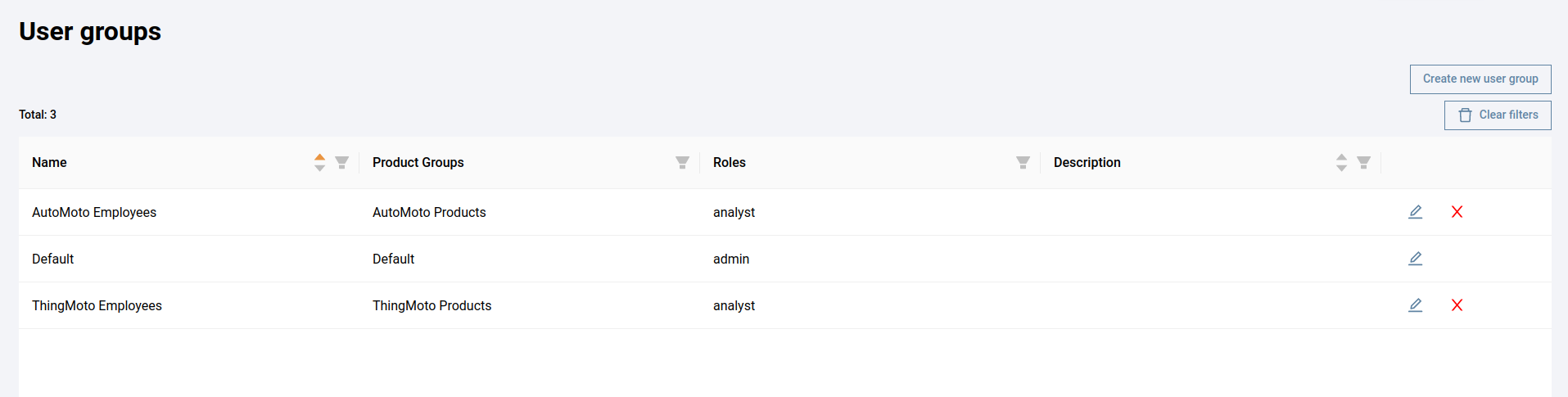
- She creates two new product groups:
AutoMoto ProductsandThingMoto Products. If there are any existing products, she moves them to their respective groups. - She then creates a new user group,
AutoMoto Employees. - She assigns
AutoMoto Employeesthe relevant users, theAutoMoto Productsproduct group, and theanalystrole. She does the same forThingMoto Employees(except she assigns itThingMoto Productsinstead ofAutoMoto Products).
Now employees of each department can only access the products and firmware of their own business unit.
Setting up a product security team¶
Hannah logs back into ONEKEY:
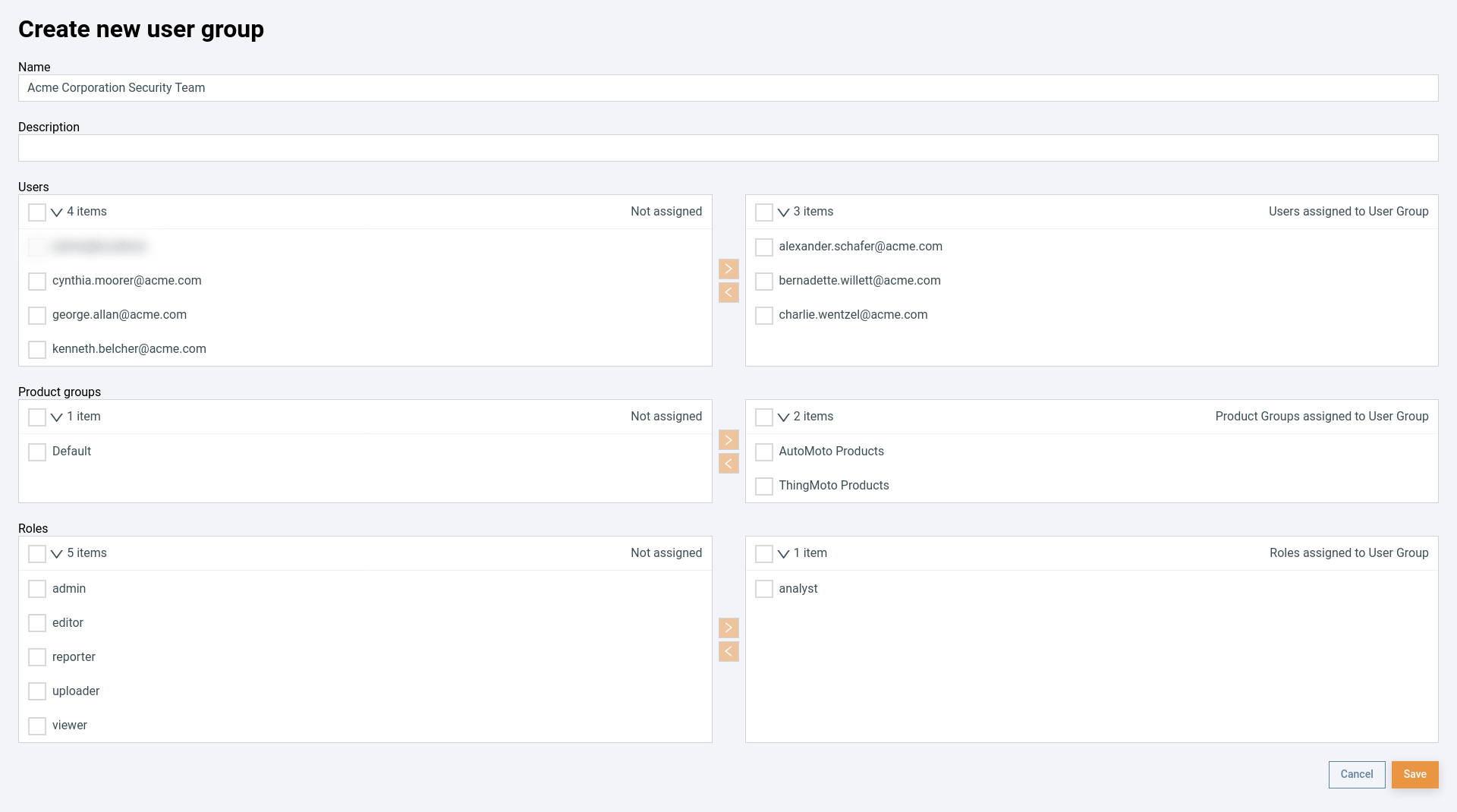
- She creates a new user group
Acme Corporation Security Team. - She assigns it the relevant users, both the
AutoMoto ProductsandThingMoto Productsproduct groups, and theanalystrole.
Now the product security team has access to the products and firmware of both business units.
Setting up a supplier¶
Hannah opens ONEKEY again:
- She creates a new user group
Supplier Technology. - She assigns it the relevant users, the
ThingMoto Productsproduct group, and theuploaderrole.
Now the third party supplier can upload firmware for the ThingMoto Products product group but has no access to the analysis results.