Firmware extraction¶
The first step in the analysis process is to retrieve data from the uploaded firmware, in other words, firmware extraction. For this the platform uses unblob, an open-source firmware extraction suite created by ONEKEY developers.
Note
If an SBOM file is attached to the firmware, the platform automatically validates it before extraction begins. Any issues with the SBOM (such as invalid or missing data) will cause the analysis to fail.
Unblob parses unknown binary blobs for over 100 different archive, compression, and file-system formats, and identifies both Known chunks and Unknown chunks.
The extraction process works as follows:
- Unblob scans the firmware for supported formats using format signatures.
- When a format is identified, the start and end offset of that valid chunk is carved to disk.
- The valid chunks are decompressed or extracted, depending on their format.
- We do the same with unidentified data between the files (the unknown chunks).
- The process is repeated recursively, with decompressed or extracted files being fed back to unblob.
Note
ONEKEY automatically reports and identifies unknown chunks composed of known content (for example padding).
Select the Extraction page in Firmware analysis view to display a list of all identified blobs.
Once the firmware is extracted, the platform moves on to Enumeration.
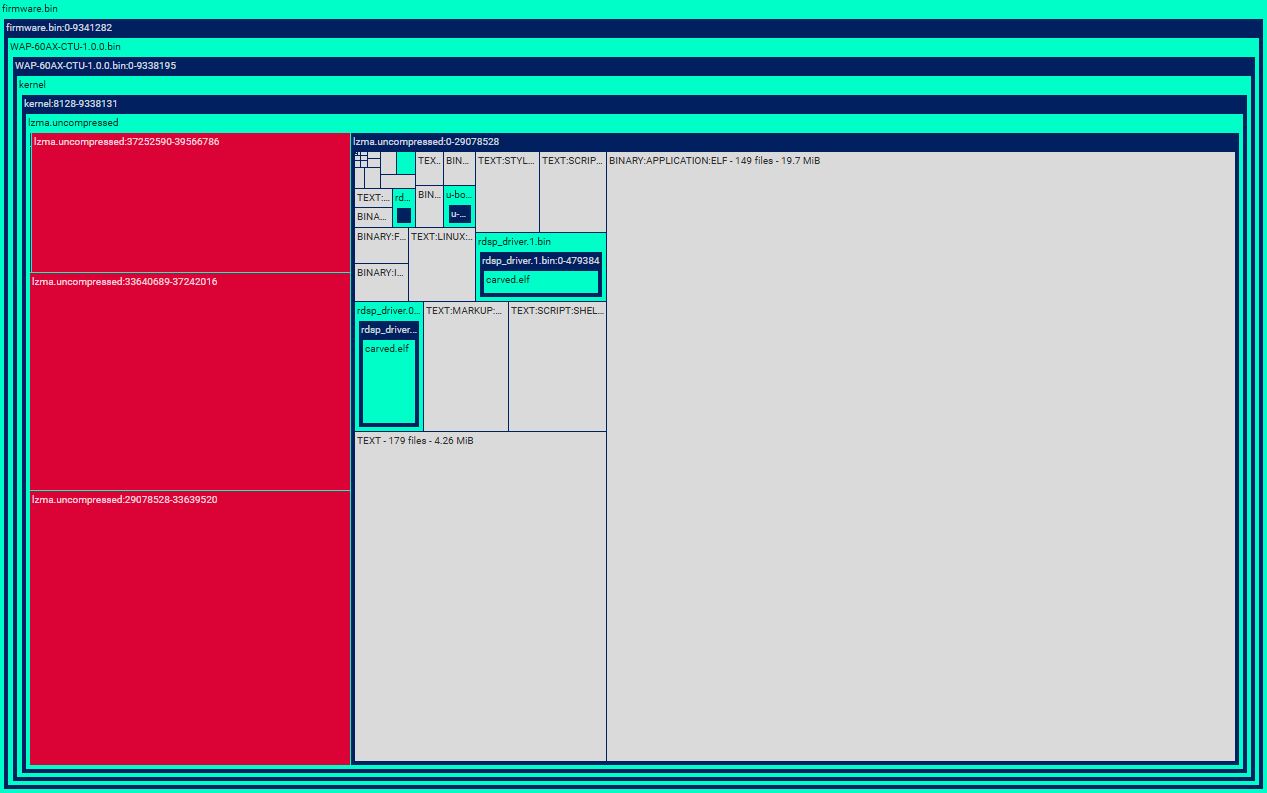
Firmware structure visualization¶
This view helps you navigate through the nested layers that compose a firmware. To view it:
- Select a firmware to enter Firmware analysis view.
- Go to Extraction.
- Select the Firmware structure tab.
Click on a file or a chunk in a lower level to reveal the underlying layer of the firmware structure.
Click on a chunk (green or blue rectangle in the visualization) to see its content. (1)
-
- If there are further levels below the chunk, the visualization zooms in on them.
- If there are no further layers, the File details opens.
To go back to a previous level click the folder's name at the top.
If you click on an unknown chunk, the Entropy chart will open.
Colors and their meaning
Red: Unknown chunk
Blue: Valid chunk
Green: File that contains chunks
Grey: File grouped by a category that does not contain chunks
ONEKEY does not show unknown chunks that it couldn't identify (or "unknown unknowns") in the visualization.