CVE matching¶
ONEKEY automatically matches Common Vulnerabilities and Exposures (CVEs) with the components found in your firmware.
CVE matching is done through Common Platform Enumeration (CPEs). Once the platform identifies the components within your firmware, it matches the CPEs against the NIST National Vulnerability Database (NVD). (1)
- In the rare case when the platform cannot find a CPE identifier, you can edit or add CPE identifiers manually by updating the 'Vendor' and 'Product' fields. This improves the CVE matching results.
CVE details¶
To see the CVEs found in a particular firmware, enter Firmware analysis view and click the CVEs tab.
Info
ONEKEY uses Automated Impact Assessment to automatically determine CVE relevance for specific firmware, so only applicable CVEs are displayed.
For a list of CVEs found in all uploaded firmware, select the Search in tab in the top menu bar and click the CVE button.
Click on a CVE to learn more about it.
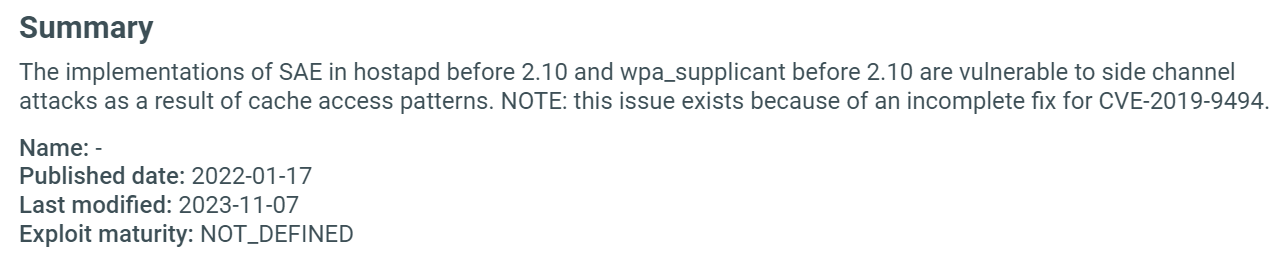
Summary¶
Short description of the vulnerability and basic information, such as the date it was published, the unofficial name given by the discoverer, CWE, and EPSS information. (1)
-
The CWE (Common Weakness Enumeration) shows the type of vulnerability associated with the identified CVE. Click on the CWE to learn more.
EPSS (Exploit Prediction Scoring System) shows the probability of a vulnerability being exploited. The greater the score the higher the chance for an exploit. The percentile means the proportion of all scored vulnerabilities with the same or a lower EPSS score.1 Click on the question mark to learn more.
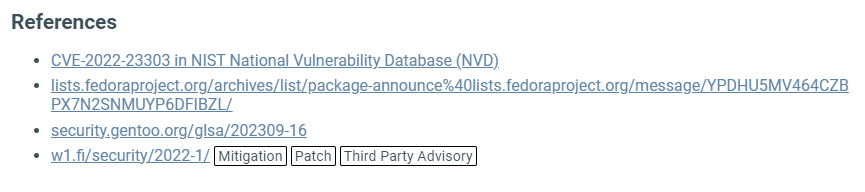
References¶
List of websites from where the platform got the displayed information, along with some further reading about the CVE.
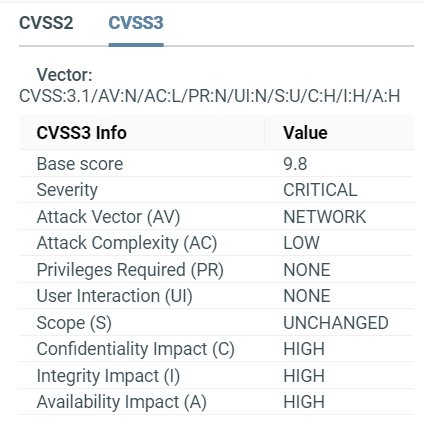
CVSS¶
CVSS stands for Common Vulnerability Scoring System; it shows the risk factor of a vulnerability by assigning it a score from 0-10 (0 means no risk, 10 means critical risk). CVSS also includes other details like attack complexity, integrity impact etc.
ONEKEY displays CVSS2 and CVSS3 vulnerability information.
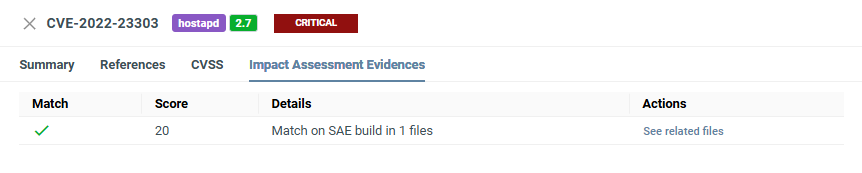
Automated Impact Assessment¶
Here you can see how the Automated Impact Assessment match score was calculated and the evidence behind the score and decision.
Calculating severity¶
Severity is based on the CVSS3 score:
| Severity | Severity Score Range |
|---|---|
| Informational | 0.0 |
| Low | 0.1-3.9 |
| Medium | 4.0-6.9 |
| High | 7.0-8.9 |
| Critical | 9.0-10.0 |