Component detection¶
Component detection is part of ONEKEY's firmware composition analysis. After extraction is complete, we detect components by analyzing the extracted files.
There are multiple methods we use to identify components:
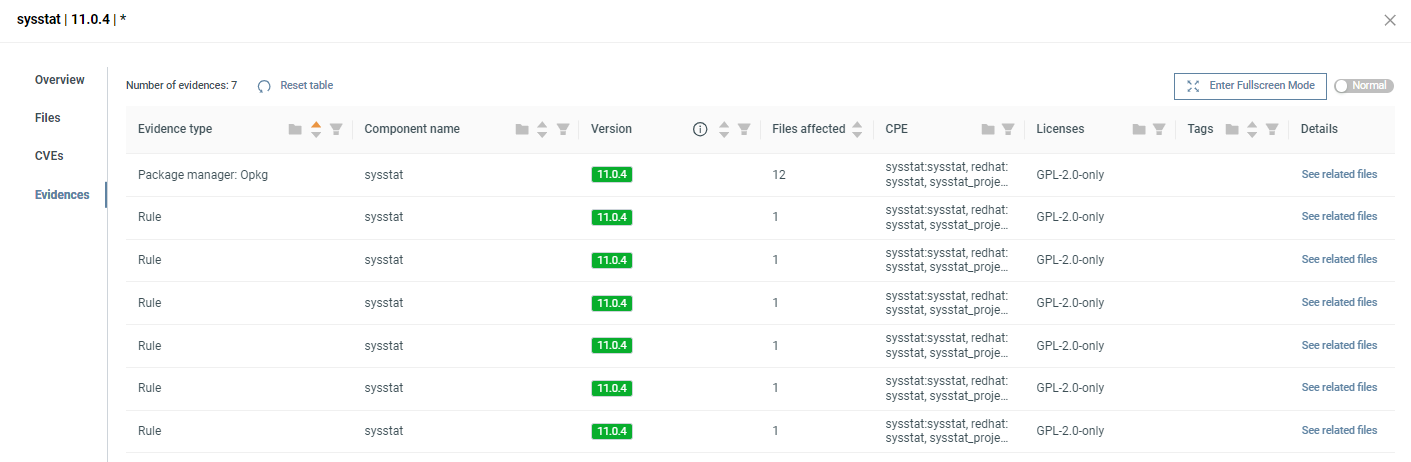
- Rules: Created by ONEKEY researchers, these rules identify components based on the file information such as file name, file type, file content, and symbols.
- Package managers: If a firmware uses a package manager, we list the components it includes. Supported package managers are: opkg, ipkg, and dpkg.
- QNX packages: If QNX is detected, we enumerate installed QNX packages to identify components.
- Lock files: If a firmware includes an application with a lock file (such as Python wheel or JavaScript package.json), we list the components it includes.
- Go binaries: These are self-describing binaries with all dependencies statically built-in. ONEKEY runs collectors to identify these built-in dependencies.
- Linux distribution: A specialized rule collects this information.
- SBOM: Imported when uploading firmware. Supported SBOM formats are: CycloneDX JSON (versions 1.2 - 1.6) and CycloneDX XML (versions 1.1 - 1.6).
- Real Time Operating Systems (RTOS): We identify and extract standard libraries, cryptographic components, and TCP/IP stacks.
Once the components of a firmware are identified, we list our findings on the Components page in Firmware analysis view. Click on a component to see more details:
- Update: The update part of the version.
- File count: Number of files a component contains.
- Vendor: Organization or entity that developed, produced, or distributed the component.
- Product: Name of the software, hardware, or firmware to which the Common Platform Enumeration (CPE) refers.
- Licenses: Open source or proprietary license information. The dropdown in edit mode lists valid SPDX license identifiers.
- Tags: A label that indicates the component's purpose or its source .
We show the methods and sources used in identifying the selected component on the Evidences tab.