Vulnerability management¶
Summary
Triage and evaluate security issues and CVEs using CVSS Environmental scores, the VEX cybersecurity standard, and SSVC assessments. Set statuses and comments to support prioritization, and filter vulnerabilities by their status.
Effective vulnerability management is key to maintaining strong cybersecurity, as it helps identify and remediate weaknesses before they can be exploited.
ONEKEY’s vulnerability management tools support the process of identifying and prioritizing security issues and CVEs, making them easier to address:
- Manually assign statuses and comments to vulnerabilities or automate the process using Analysis Profile.
- Perform advanced triage through CVSS 1 Environmental scoring, VEX 2, and SSVC 3 assessments.
- Use the Copy assessment function to transfer an assessment from a previous firmware version to a new one, eliminating repetitive manual work.
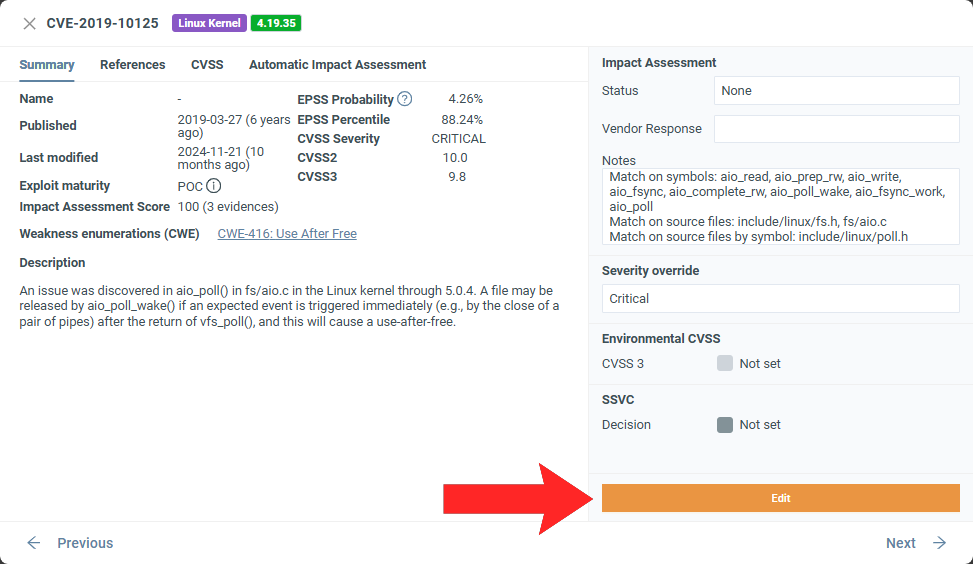
Assess a vulnerability¶
As part of the analysis process, the platform automatically performs CVSS scoring, assigns a severity level, and sets the status to NONE or Not Affected – based on Automated Impact Assessment – for each vulnerability. If supporting evidence is available for the impact assessment decision, it is displayed under Notes and the Automated Impact Assessment tab.
To override automatic decisions and set a manual assessment:
- Select a firmware to enter Firmware analysis view.
- Click either the CVEs or Issues tab.
- Select a vulnerability to open the CVE/issue details.
- Click Edit.
To update multiple vulnerabilities, check the box next to the issues or CVEs and click Set assessment.
To track past changes, see the Audit Trail page in Firmware analysis view.
Notes vs. Comments
Notes are associated with the vulnerability and can be automatically updated by Automated Impact Assessment; they do not appear in the Audit Trail unless a change has been made.
Comments, on the other hand, appear exclusively in the Audit Trail, can only be added manually, and are not linked to the vulnerability itself – they are to explain why an update was made.
Security standards¶
To follow recommended practices inspired by VEX and CycloneDX v1.6, set the Status, Vendor Response, and Justification fields.
Note
The Justification field only appears when you select a relevant status.
To perform an SSVC assessment, click Edit next to the relevant section and complete the SSVC calculator.
SSVC is especially useful when teams need to prioritize vulnerabilities based on more than just severity scores, as it incorporates contextual and stakeholder-specific factors. A good example would be organizations operating critical infrastructure (e.g., healthcare, energy, finance), where an exploitation could directly impact safety or disrupt core services.
A CVSS Environmental score reflects how a vulnerability’s impact and exploitability can vary depending on the deployment environment. For example, if your client is operating a public-facing server, a vulnerability can be more exposed there than in your isolated test environment; you can record this by assigning a higher CVSS Environmental score than the base score.(1)
- You can't set environmental score for CVEs that don't have a base score.
To add a CVSS environmental score, click Edit next to the relevant section and use the CVSS calculator. After you fill out the calculator, the vulnerability’s severity will automatically update to reflect the environmental score, even if you previously set the severity manually with Severity override.(1)
- If you try to set different severity levels using both the override and the environmental score calculator in the same workflow, the severity override will take precedence.
VEX Import¶
Vendors, distributors, or suppliers can provide a VEX file containing a detailed vulnerability assessment. Importing such a file helps streamline vulnerability management and triage by automatically updating CVE assessment fields with the corresponding vendor responses.
To import a VEX file:
- Select a firmware to open Firmware analysis view.
- Go to the CVEs page.
- Click Import VEX.
- Follow the on‑screen instructions.
You can select which CVEs you want to update; you do not need to update all of them.
After the file is imported, the platform adds an automatic comment to each affected CVE about the update.
Note
- Supported file formats are: OpenVEX JSON, CSAF JSON, CycloneDX JSON. The supported versions are listed in the VEX upload dialog.
- On the import screen, all affected CVEs are displayed, whether they were manually edited before or not.
You can upload multiple VEX files at once. Only valid files are accepted; if an uploaded VEX file is invalid, the platform displays an error message and ignores the file.
If multiple uploaded VEX files affect the same CVE, the platform prompts you to choose which file to use for the update. To apply more than one VEX file to a single CVE, import them one by one rather than in a batch.
You can choose between Strict and Relaxed import modes, depending on how precisely you want to match the data.
Strict vs. Relaxed mode
Strict mode: The CVE ID and component details must match.
Relaxed mode: Only the CVE ID must match.
VEX Export¶
Exporting VEX information can, for example, support compliance with certain cybersecurity regulations (such as the Cyber Resilience Act), as it provides documented statements of vulnerability assessments and mitigations.
To export a VEX‑enhanced SBOM:
- Select a firmware to open Firmware analysis view.
- Click Download SBOM.
- For the SBOM format, select CycloneDX.
- Select which details to include using the checkboxes.
Assign a status¶
There are two main status categories you can choose from: closed and open. (1)
-
Open statuses:
- Triage
- Focus
- None (default status)
Closed statuses:
- Accepted risk
- Deferred
- False positive
- Fixed
- Not affected (set by Automated Impact Assessment for non-relevant CVEs)
Vulnerabilities with a closed status do not appear in the CVE or issue tables by default. To see closed vulnerabilities, uncheck Show only CVEs/issues with open status.
You can only set a status for issues/CVEs in the Firmware analysis view of a specific firmware, not on the global pages.
Override severity¶
ONEKEY automatically assigns a severity to each vulnerability based on the overall CVSS 3 score. You can override this to account for factors that are unique to your environment. To do so, select a new severity from the Severity override dropdown. The CVE/issue table will refresh once you close the details window.
Severity scores
| Severity | Severity Score Range |
|---|---|
| Informational | 0.0 |
| Low | 0.1-3.9 |
| Medium | 4.0-6.9 |
| High | 7.0-8.9 |
| Critical | 9.0-10.0 |
Copy assessment¶
Use this feature to copy the vulnerability assessment from one firmware analysis to another.
Tip
This feature can be particularly useful when uploading a new version of a previously analyzed firmware.
The copy process:
- Navigate to the Firmware analysis view of the target firmware.
- Select either the Issues or CVEs page, depending on what you want to copy.
- Click on the Copy assessment button.
- Choose a source firmware in the popup by clicking Use as source.
- Select a pairing method and specify which vulnerability assessments to copy.
- Click Copy selected assessments.
Strict vs. Relaxed mode
Security Issues
Strict mode: Only exact matches are considered, meaning all relevant details and the complete file path must be identical.
Relaxed mode: The relevant details must be identical, but only the file name - not the entire file path - needs to match.
CVEs
Strict mode: Only exact matches are considered, meaning all the relevant details must match.
Relaxed mode: Only the CVE ID and the component name must match.
-
Common Vulnerability Scoring System. A standardized framework for assessing the severity of software vulnerabilities by assigning a score from 0 to 10 based on factors like exploitability, impact, and environmental context. ↩
-
Vulnerability Exploitability eXchange. A form of a security advisory. VEX documents are machine readable and support more effective use of Software Bills of Materials (SBOM) data. ↩
-
Stakeholder-Specific Vulnerability Categorization. A decision-tree-based security framework that considers real-world factors like exploitation status, mission impact, and stakeholder roles, rather than relying solely on generic severity scores. ↩